NAXSI: Nginx Anti XSS & SQL Injection.
Testing XSS and SQL injection to the Nginx server
INTRODUCTION TO NAXSI
Naxsi comes with its own core ruleset and is extensible with user-specific rulesets. The configuration takes place in the Nginx context. Thanks to scores for individual rules and customizable thresholds for block actions, the WAF can be adapted to different environments and web applications.
Naxsi can check different values, such as URLs, request parameters, cookies, headers, or the POST body, and it can be switched on or off at location level in the Nginx configuration. Automatic whitelist creation makes it easy to deploy the firewall upstream and rule out 100 percent of false positives. Other tools, such as NX-Utils and Doxi, facilitate administration, report generation, and ruleset updates.
Naxsi comes with NX-utils, which is very useful for generating whitelists and reports. First, the NX-utils collection includes intercept mode, which allows Naxsi to save requests blocked by the WAF for future reports and whitelists in a database, and report mode, which visualizes the stored events. NX-Utils is currently under construction and will provide improved report processing and filtering to analyze the WAF events more precisely in a later version.
Modes: Live vs. Learning
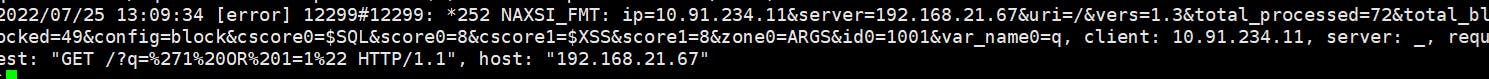
Naxsi can operate in two modes: Live and Learning (Figure 3). Like any WAF or IDS, Naxsi must be adapted for the application. Developers can take very different approaches when programming web applications. For instance, 2KB cookies with large chunks of disorganized data are not uncommon and push even experienced WAF admins to the brink of madness. For these cases, Learning mode allows you to test an application fully behind a protected test domain and generate appropriate whitelists from the queries and events, which you can then feed to an active WAF in Live operations.
In Learning mode, requests are registered but not blocked. Whitelists can be generated from the false positives to prevent them from occurring in Live operation.
INSTALLATION OF NAXSI AND INTERGATION WITH NGINX
Install required dependent packages
yum install -y perl perl-devel perl-ExtUtils-Embed libxslt libxslt-devel libxml2 libxml2-devel gd gd-devel GeoIP GeoIP-devel
Check your nginx version so that we can download the same version to compile modules with naxsi.
nginx -v
wget http://nginx.org/download/nginx-1.20.1.tar.gz
Download Perl Compatible Regular Expressions:
wget https://udomain.dl.sourceforge.net/project/pcre/pcre/8.40/pcre-8.40.tar.gz --no-certificate-check && tar xzf pcre-8.40.tar.gz
Downioad zlib library:
wget https://zlib.net/fossils/zlib-1.2.11.tar.gz && tar xzf zlib-1.2.11.tar.gz
Download openssl :
wget https://www.openssl.org/source/openssl-1.1.0f.tar.gz && tar xzf openssl-1.1.0f.tar.gz
Download NAXSI :
wget https://github.com/nbs-system/naxsi/archive/master.zip && unzip master.zip
Head over to the nginx folder that we downloaded earlier and configure the below modules in the nginx directory.
./configure --prefix=/etc/nginx \
--sbin-path=/usr/sbin/nginx \
--modules-path=/usr/lib64/nginx/modules \
--conf-path=/etc/nginx/nginx.conf \
--error-log-path=/var/log/nginx/error.log \
--pid-path=/var/run/nginx.pid \
--lock-path=/var/run/nginx.lock \
--user=nginx \
--add-module=../naxsi-master/naxsi_src --group=nginx \
--build=CentOS \
--builddir=nginx-1.14.0 \
--with-select_module \
--with-poll_module \
--with-threads \
--with-file-aio \
--with-http_ssl_module \
--with-http_v2_module \
--with-http_realip_module \
--with-http_addition_module \
--with-http_xslt_module=dynamic \
--with-http_image_filter_module=dynamic \
--with-http_geoip_module=dynamic \
--with-http_sub_module \
--with-http_dav_module \
--with-http_flv_module \
--with-http_mp4_module \
--with-http_gunzip_module \
--with-http_gzip_static_module \
--with-http_auth_request_module \
--with-http_random_index_module \
--with-http_secure_link_module \
--with-http_degradation_module \
--with-http_slice_module \
--with-http_stub_status_module \
--http-log-path=/var/log/nginx/access.log \
--http-client-body-temp-path=/var/cache/nginx/client_temp \
--http-proxy-temp-path=/var/cache/nginx/proxy_temp \
--http-fastcgi-temp-path=/var/cache/nginx/fastcgi_temp \
--http-uwsgi-temp-path=/var/cache/nginx/uwsgi_temp \
--http-scgi-temp-path=/var/cache/nginx/scgi_temp \
--with-mail=dynamic \
--with-mail_ssl_module \
--with-stream=dynamic \
--with-stream_ssl_module \
--with-stream_realip_module \
--with-stream_geoip_module=dynamic \
--with-stream_ssl_preread_module \
--with-compat \
--with-pcre=../pcre-8.40 \
--with-pcre-jit \
--with-zlib=../zlib-1.2.11 \
--with-openssl=../openssl-1.1.0f \
--with-openssl-opt=no-nextprotoneg \
--with-debug \
Install the GCC modules :
yum install gcc-c++
Compile the modules:
make
make install
Now let's create a symlink for /usr/lib64/nginx/modules to /etc/nginx/modules directory, so that you can load dynamic modules in nginx configuration like this load_module modules/ngx_foo_module
sudo ln -s /usr/lib64/nginx/modules /etc/nginx/modules
Check the configuration of nginx :
sudo nginx -t
Enable nginx and reload daemon.
systemctl daemon-reload
systemctl enable nginx
systemctl start nginx
Head over to naxsi-master folder and copy naxsi_core.rules file to /etc/nginx
cp naxsi_core.rules /etc/nginx
Go to nginx config file and add these two lines like shown below:
include /etc/nginx/naxsi_core.rules;
include /etc/nginx/naxsi.rules;
You might have realised that, naxsi.rules doesn’t present in /etc/nginx/ folder. So a we should create the file
vi /etc/nginx/naxsi.rules
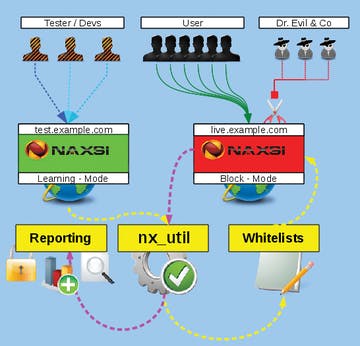
As I have already mentioned in the beginning that naxsi has 2 rule. In this document I am going to use LIVE mode to block all the payloads. By heading over to /naxsi.rules and commenting out the LEARNING MODE
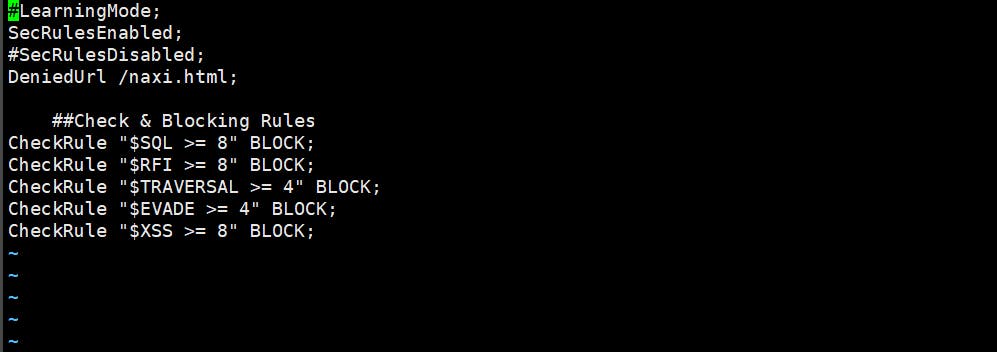
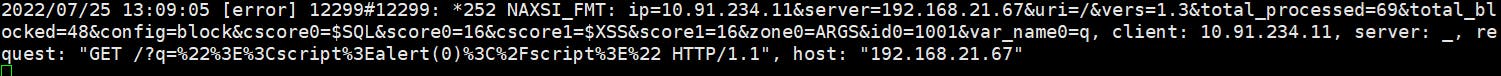
Testing XSS scripting on the website.
As we can see there is a payload in the URL, As I have enabled the LIVE mode, it blocks the payload and redirects to the 404 error page generating a log.
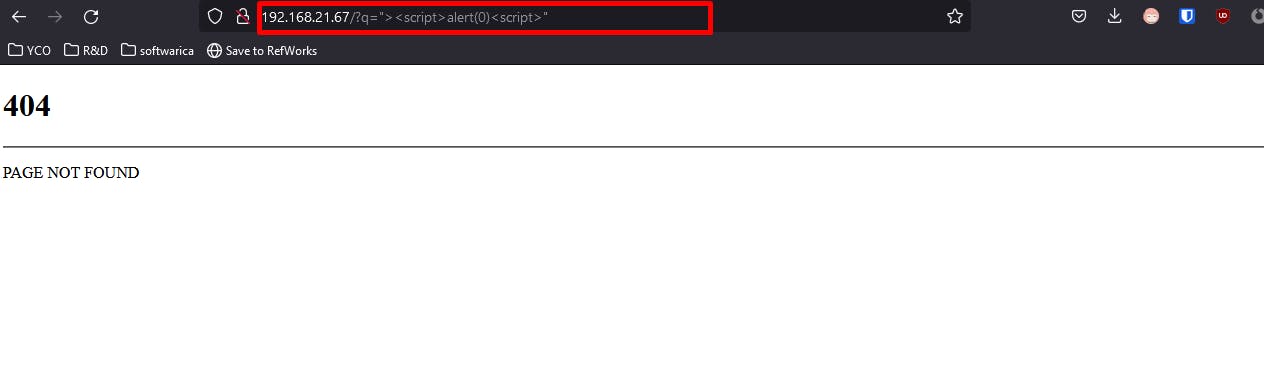
As NAXSI is a third party integreation to NGINX, so all the logs from NAXSI is sent to error log of NGINX
Testing SQL injection on the website.
As we can see there is a payload in the URL, As I have enabled the LIVE mode, it blocks the payload and redirects to the 404 error page generating a log.
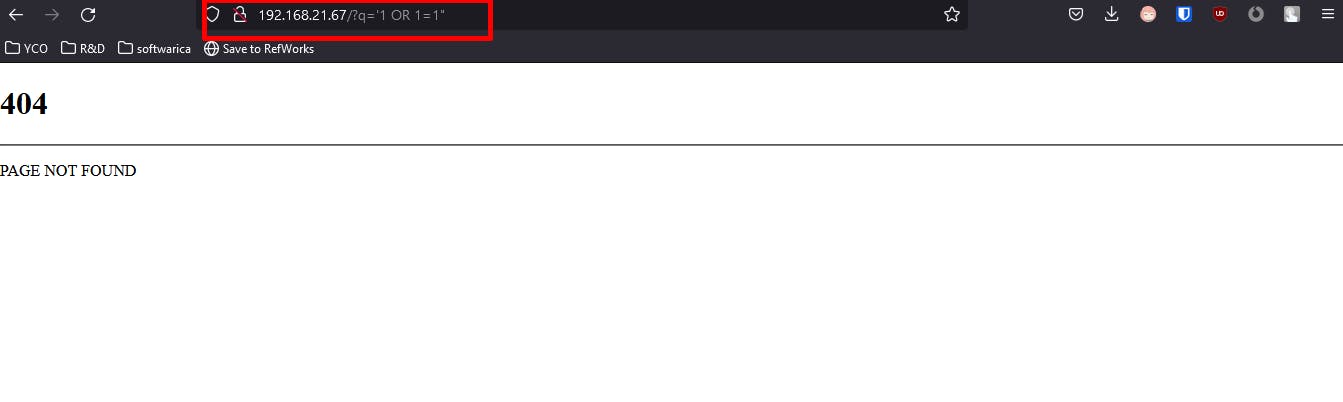
As NAXSI is a third party integreation to NGINX, so all the logs from NAXSI is sent to error log of NGINX