Table of contents
INTRODUCTION
This blog is about the journey of CCNP, and CCIE security on layer 2 attacks. In this blog, I will cover the DHCP starving and rouge attacks.
Below is the simple topology we are going to demonstrate the attacks.
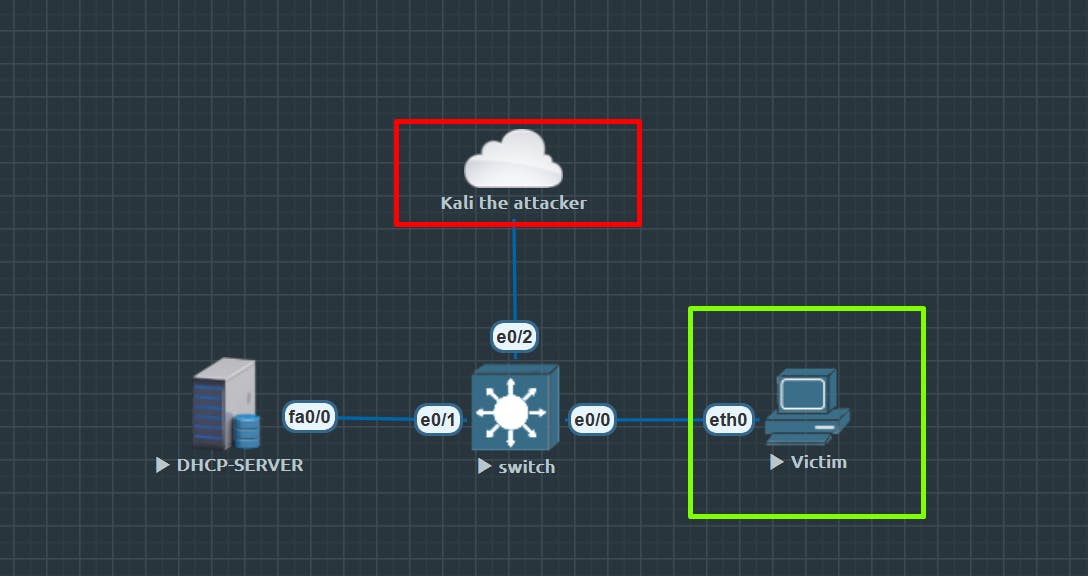
CONFIGURATION
Let's head over to the DHCP server and configure our interface fa0/0:
interface fastEthernet 0/0
ip address 192.168.1.1 255.255.255.0
no sh
no cdp run
Let's make a DHCP pool of our server and start to give out IPs to all the end devices.
ip dhcp pool test-1
network 192.168.1.0 /24
dns-server 8.8.8.8
default-router 192.168.1.1
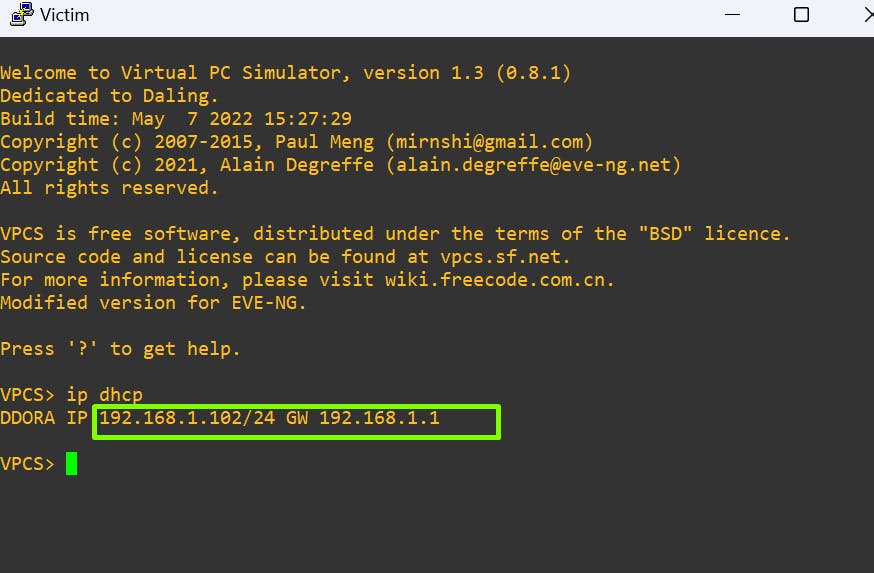
Let's verify if both the victim and attacker machine if they got the IP from the server.
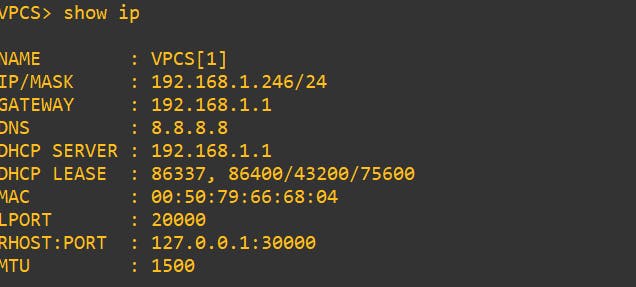
victim pc
Attacker pc
Voilà! there you go they both got the same network IP.
DHCP Starving Attack

So what is DHCP Starving Attack you make ask, let's take an example here? So imagine it's a very hot day outside and you want a drink cold drink so you head out to your favorite store and go to the beverage section you see there aren't any drinks so you go out to another store and buy it at a high price and then you realize this another store is the person who brought all the drinks. It's really a weird analogy I know so bear with me.
In this analogy, your fav store is the DHCP server, cold drink is the IP, you are the victim and the other store is the attacker.
So what's happening here is that, the attacker impersonates new devices every time and asks for a new IP until the server runs out of IPs. Hence no legitimate devices can get the IP and it won't work, now imagine your server is running in DHCP and they can't get any more ip after the lease time (This is the length of time that the client can use the IP address it has been assigned) and the server won't work. So how can we fix it? simply don't use DHCP. Lmao, I am just kidding. First, I am gonna show how a DHCP starving attack can be done.
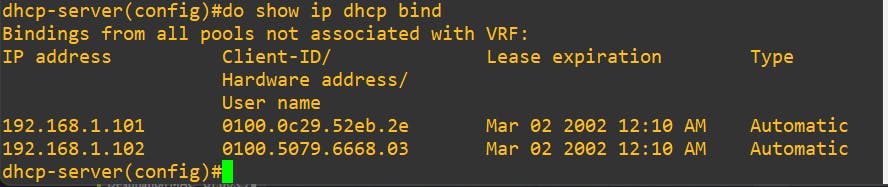
Before: We can see that the IP that has been bound to the end devices are only 2.
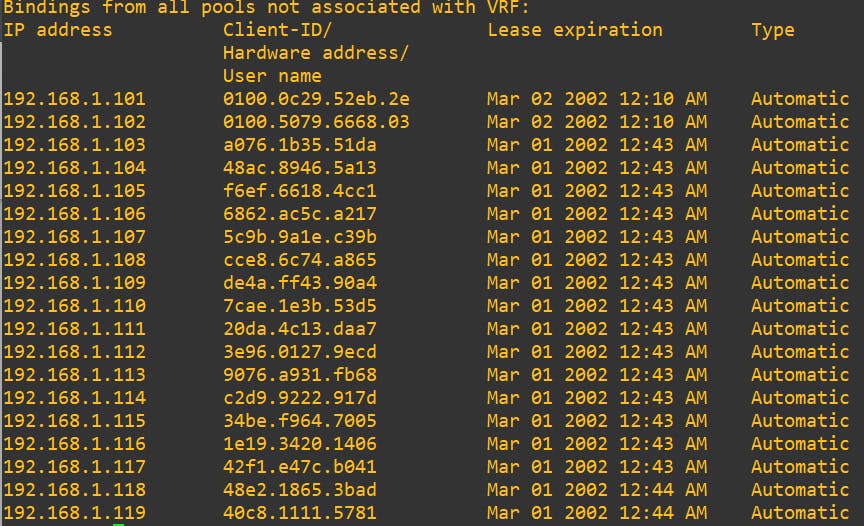
After: I am going to use a tool name yersinia to send discovery packets to the server to take all the IPs that it has and successfully attack.
Here we can see that the IP has been bound to all the "victim" devices.
DHCP Rouge Attack
As Akshaya Kumar has explained from the figure. To simplify it, let's take our cold drink analogy. So as always you are going to your fav store but someone has been able to make a replica of the store to steal your credit card details, you are innocent of not being able to differentiate the store you will go to and buy your drink with your credit card.
So what is happening here then? You are the victim, the replica store is the rouge server and your credit card details are the information of your device.
So what's the big deal, my IP has only been changed and I can still surf the internet. Ugh! the attacker will have all your details from what you have surfed to what password you are using to everything.
So in technical terms, A rouge server is nothing but the replica of the DHCP server so that the end devices can get IP from the attacker server and the attacker will have the information of all the end devices. Without further ado, let's jump into the example.
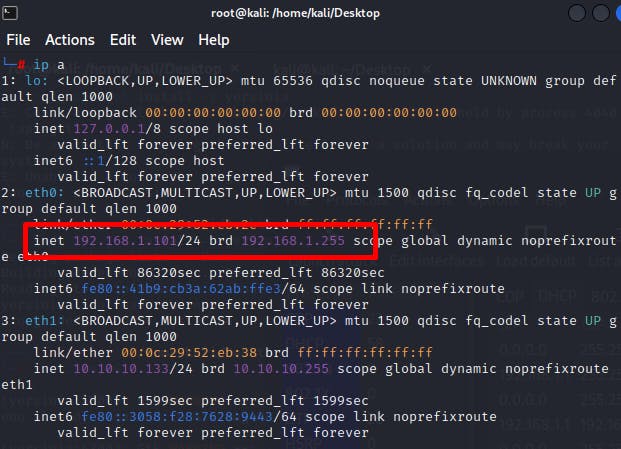
Before: Let's see the actual IP of our victim.
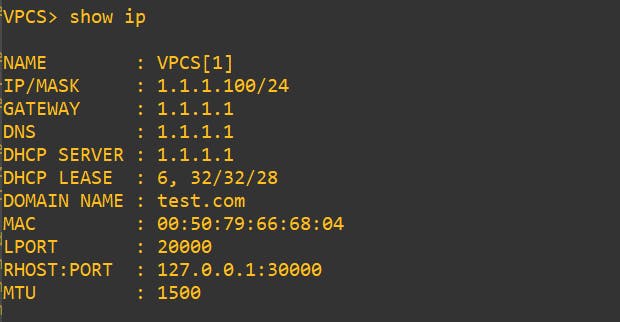
After: Let's make our own rouge server and see how a victim won't be able to differentiate which server is real. Note: To make this happen I have changed my ip on the kali machine.
Victim pc
Voilà again! there you go the victim's PC got the IP from the rouge server.